The following is provided from Microsoft Security and Compliance blogs at TechCommunity:
In talking to our customers, we learned that IT and security operations roles need a more efficient way to contain a data spill by quickly identifying the impacted content and taking immediate action to remediate the risk.
Unfortunately, in the past, this process involved several different tools such as content search, audit log search and executing different PowerShell cmdlets.
Today, we are excited to share new data investigation capabilities in Office 365 that is available in preview. With these new capabilities in Office 365, you can search for sensitive, malicious, or misplaced data across Office 365, investigate what happened, and take the appropriate actions to remediate the spillage.
Read further to understand what data investigation capabilities in Office 365 can do:
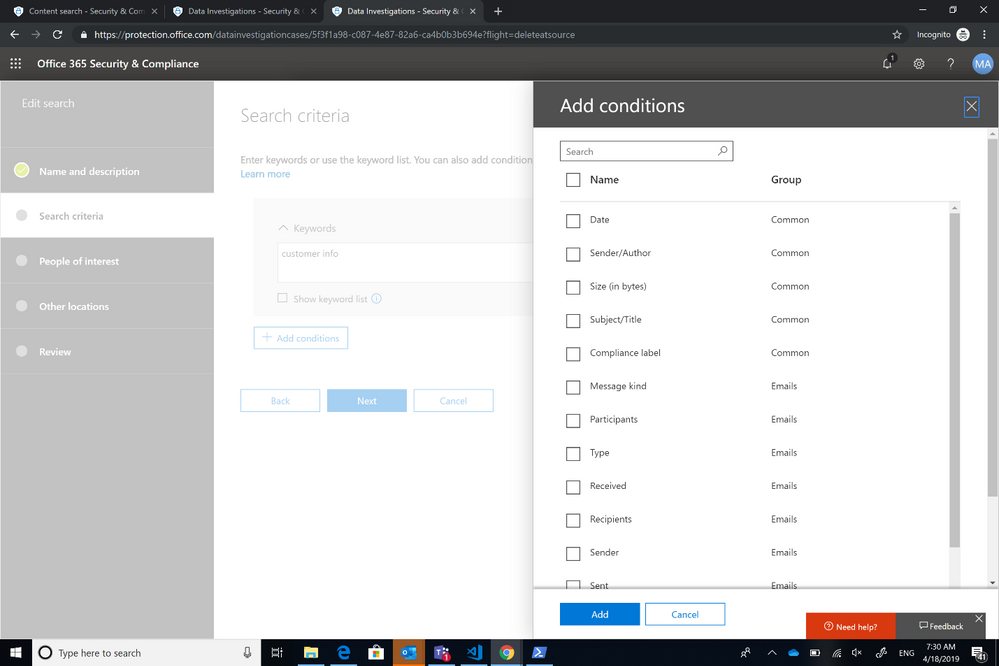
Advanced search
Target relevant content across Office 365. Quickly identify potential sources of both personal and shared content locations. You can also triage data with conditions, key words and advanced search functionality to cull initial collection to a smaller set. Once evidence is collected to a reasonable data set, you can process and validate the content.
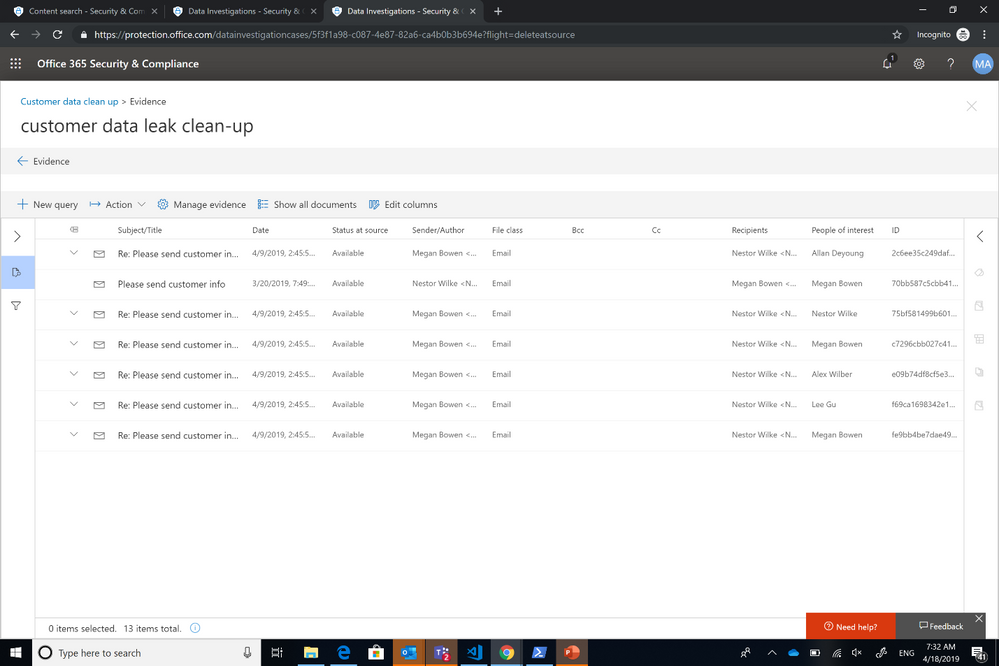
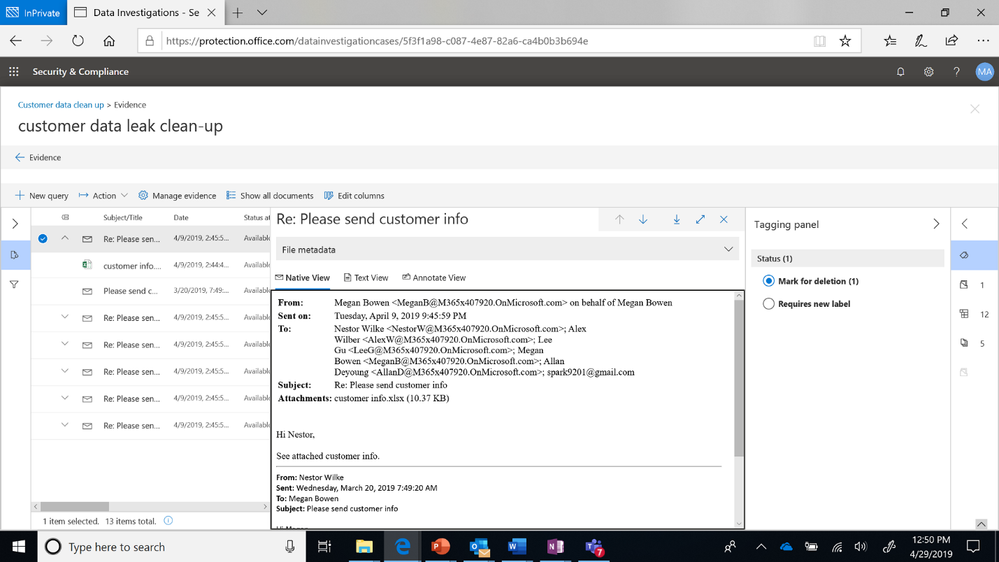
Review and investigate the data
Once you are ready to process and validate the impacted content, you can review individual documents and evaluate the data to determine if further action is required.
Remediate risk by taking immediate action
Finally, you can remediate and mitigate the incident of a data spill and limit damage to the organization by deleting the impacted data to prevent end users from accessing the content. Today this is done through PowerShell but we plan on providing a UI experience at the end of May.
Get started today
Review our supporting documentation and try the data investigation capabilities in Office 365 in Preview today.
Also, let us know what you think! We want to hear from you. Fill out this short survey for us if you are interested in us reaching out to you.
Related Posts
The above was provided from Microsoft Security and Compliance blogs at TechCommunity